In modern enterprise integrations, protecting sensitive credentials such as API keys, client secrets, and certificates is essential. Traditional methods—hardcoding secrets in X++ code, storing them in parameters, or saving them in plain-text tables—introduce significant security and compliance risks.
Azure Key Vault solves this challenge by providing a secure, centralized, and encrypted store for all secrets. With native support in Dynamics 365 Finance and Operations (D365 F&O), developers can retrieve secrets programmatically without exposing them in code.
This guide provides a clear overview of Azure Key Vault, explains what it is, and walks through the complete process of integrating Key Vault with D365 F&O, including configuration steps and X++ examples.
Why use Azure Key Vault with D365 F&O?
Using Azure Key Vault as your secret management solution provides several core advantages:
1. Eliminates hardcoded secrets
Credentials are no longer stored in X++ code, configuration forms, or custom tables.
2. Secure, encrypted storage
Secrets are stored using Azure’s industry-leading encryption, including support for Hardware Security Modules (HSMs).
3. Supports secret rotation
Credentials can be updated or regenerated without modifying or redeploying code.
4. Role-based access control (RBAC)
Access is governed through Azure Active Directory, ensuring only approved services and users can retrieve secrets.
Take control of your business operations
Discover how Confiz services can simplify your complex workflows and improve decision-making.
Get a Free Quote5. Compliance & auditing
Azure Key Vault meets major compliance standards (ISO, SOC, GDPR) and provides detailed access logs for monitoring and audit trails.
| Benefit | Description |
|---|---|
| No Hardcoded Secrets | Secrets are not stored in X++ or parameters. |
| Secure Storage | Secrets are encrypted using Azure HSM. |
| Secret Rotation | Secrets can be updated without code changes. |
| Role-Based Access | Access controlled using Azure AD and RBAC. |
| Compliance | Supports ISO, SOC, and GDPR security compliance. |
| Auditing | Logs access to secrets for monitoring. |
Azure Key Vault architecture (High-level)
Understanding the Azure Key Vault architecture helps clarify how D365 F&O interacts with secured secrets:
- Azure Active Directory (AAD) authenticates D365 via an App Registration.
- D365 uses the App Registration’s Client ID and Secret to request access.
- At runtime, D365 retrieves secrets from Key Vault in Azure using a secure REST API.
- Secrets are never stored in application code, configuration parameters, or database tables.
Read more: Is your Dynamics 365 environment really secure? Uncover the hidden risks
This provides a clean separation between application logic and confidential credentials.
Step 1: Create Azure Key Vault
To configure Azure Key Vault:
- In the Azure Portal, select Create a resource.
- Search for Key Vault, then select it.
- Click Create.
- Fill in the required details:
- Name: e.g., Contoso-Vault2
- Subscription
- Resource Group
- Location
- Keep default encryption settings.
- Click Create to deploy.
This completes the first part of setting up the vault.
Step 2: Create a secret in Azure Key Vault
Once your vault is deployed:
- Open your Key Vault (e.g., Contoso-Vault2).
- Locate the Vault URI — example:
https://contoso-vault2.vault.azure.net/ - Navigate to Secrets → Generate/Import.
- Add your secret value (e.g., API key, client secret).
This prepares the Key Vault for use by D365 F&O.
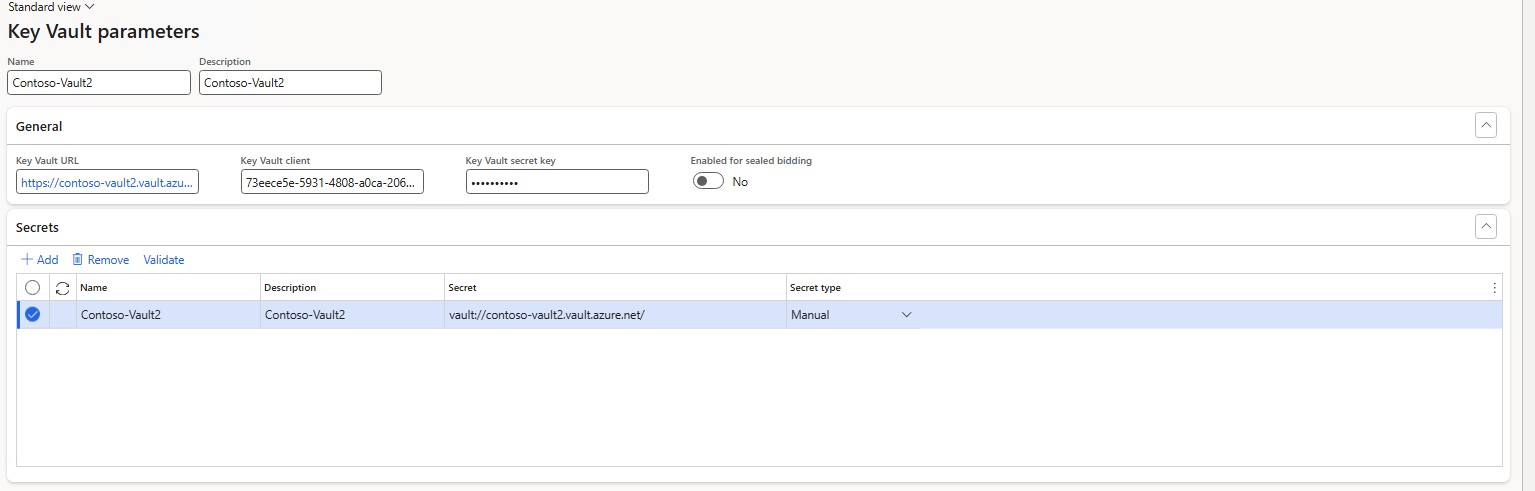
Step 3: Configure Azure Key Vault in D365 F&O
In D365 F&O, navigate to:
System administration → Setup → Azure Key Vault parameters
Enter:
| Field | Value |
| Client ID | Azure App Registration ID |
| Client Secret | Secret stored in Azure Key Vault |
| Key Vault URL | https://contoso-vault2.vault.azure.net/ |
Save the settings and validate the connection.
This step authorizes D365 to securely read from Azure Key Vault.
Step 4: Add secret references in D365 F&O
In the Azure Key Vault Parameters page:
- Add a row for each secret you want D365 to read.
- Enter the name exactly as defined in Key Vault.
- Click Validate to test connectivity.
Once validated, D365 can retrieve the secret at runtime.
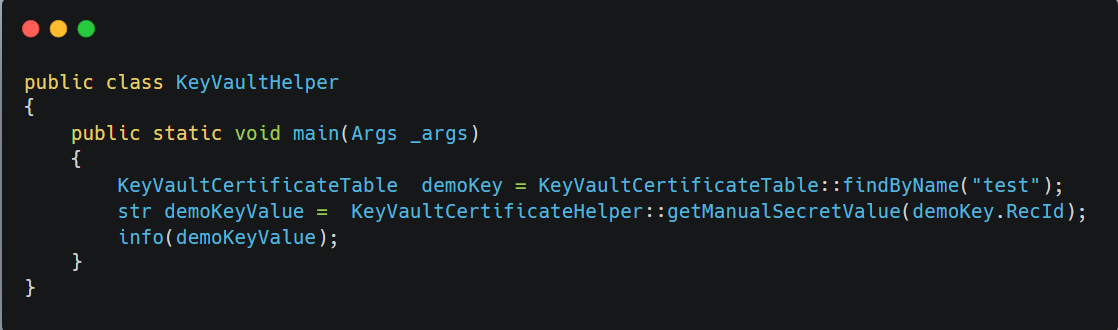
Retrieve secret in X++
Below is a typical X++ example for retrieving secrets:
Best practices for Azure Key Vault in D365 F&O
To maintain a secure and reliable implementation of Azure Key Vault with D365 F&O, follow these recommended practices:
1. Use secret versioning
Version secrets to prevent accidental overwriting and to support controlled rollbacks when needed.
2. Apply RBAC permissions
Restrict access using Azure Role-Based Access Control so only authorized applications and users can read or modify secrets.
Accelerate growth at an unprecedented pace
Discover how Confiz can help you take control of your daily operations, increasing growth and revenue.
Book a Free Consultation3. Rotate secrets regularly
Update credentials periodically to comply with internal security policies and reduce exposure risks.
4. Leverage Key Vault for all integrations
Ensure every integration—especially those that consume external APIs—retrieves credentials from Azure Key Vault rather than from local configuration.
5. Avoid storing secrets in parameters or custom tables
Do not store sensitive credentials in SysParameters, custom tables, or hardcoded X++ logic.
Following these practices ensures your secret management approach remains secure, scalable, and compliant with enterprise standards.
Conclusion
Azure Key Vault delivers a secure, centralized, and scalable approach to managing credentials for Dynamics 365 Finance and Operations. By integrating Key Vault with D365 F&O, organizations remove the risks tied to hardcoded secrets, maintain compliance with security standards, and ensure sensitive values are retrieved only through controlled, audited access. This approach strengthens overall system security while simplifying long-term maintenance across integrations and customizations.
For guidance on implementinag Azure Key Vault with D365 F&O, contact marketing@confiz.com.










